Integrating Jamf Connect Verify with OneLogin
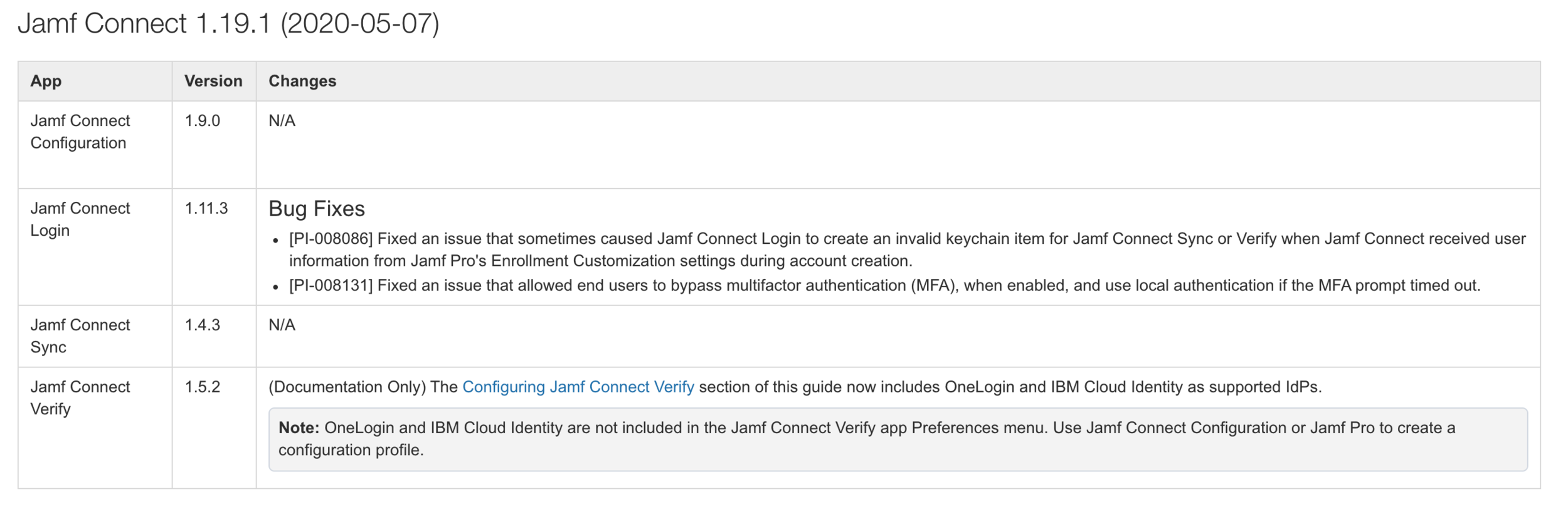
UPDATE: With the release of Jamf Connect 1.19.1, released on May 7, 2020, Jamf officially added support for Jamf Connect Verify and OneLogin. With Jamf Connect Verify 1.5.2 (released with Jamf Connect 1.19.1—confusing, I know), administrators can specify OneLogin and IBM Cloud Identity as supported IdPs wit the OIDCProvider key value (e.g. OneLogin, IBMCI). Jamf now also includes the need to specify “MFA” for ROPGSuccessCodes when configured Jamf Connect Verify for OneLogin use.
Jamf Connect is a product offering by Jamf that offers enterprise clients the ability to offer just-in-time account provisioning as well as password synchronization with supported identity providers (IdP). Account provisioning is handled by Jamf Connect Login while password synchronization is accomplished with Jamf Connect Sync and Jamf Connect Verify. Depending on which IdP you are utilizing, this will dictate whether you will need Jamf Connect Sync or Jamf Connect Verify. As of Jamf Connect Version 1.15.0, Jamf supports the following IdP services:
Google Identity
IBM Cloud Identity
Microsoft Azure AD
Okta
OneLogin
PingFederate
As you can see in the provided table below, OneLogin is only supported for Jamf Connect Login and Jamf Connect Configuration. According to Jamf’s product documentation, “Jamf Connect Configuration is an app that allows administrators to automatically configure and create computer configuration profiles for Jamf Connect apps.” This is particularly useful when IT administrators are building configuration profiles for Jamf Connect. So then, it seems, that OneLogin does not offer password synchronization capabilities, right? Sort of. I mean, yes. Let me explain.
In the below section, we will cover the steps to successfully integrate Jamf Connect Verify with OneLogin. For instructions on configuring Jamf Connect Login with OneLogin, please refer to the Jamf Connect Administrator's Guide.
Editor’s Note: In general, following Jamf’s product documentation is integral to a successful implementation of their products. The purpose of this post is to shed light on a specific setting that is not yet captured in the Jamf Connect Administrator's Guide for Version 1.15.0. I have contacted Jamf and hope that the Required Key-Value Pair for Jamf Connect Verify are updated in a future release of Jamf Connect.
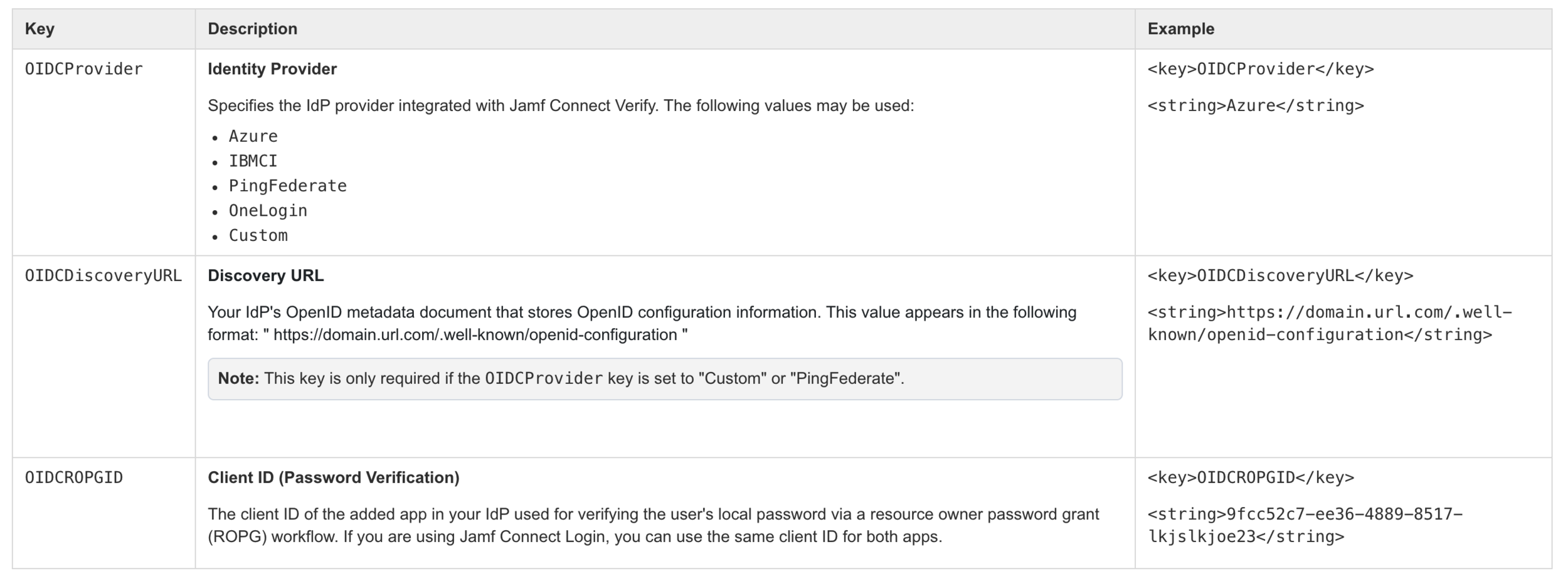
Required Key-Value Pair
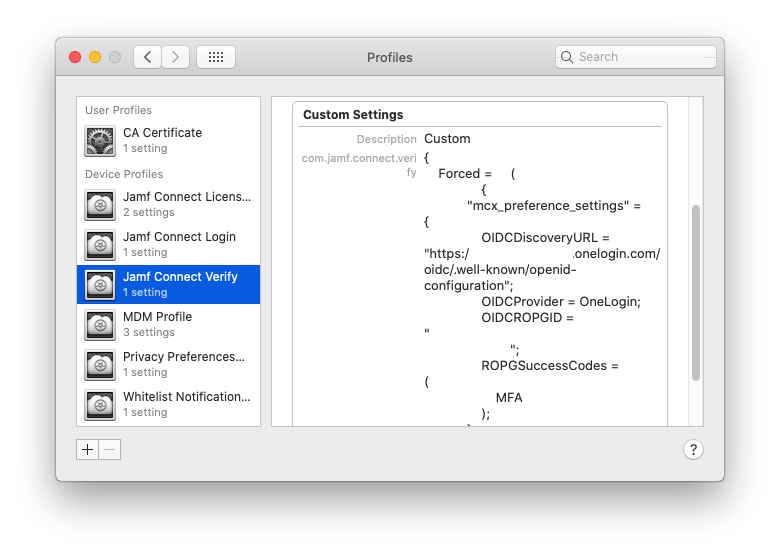
With the information detailed above, you are able to configure a property list file using a text editor of your choice. While the OIDCProvider key above specifically calls out “Azure,” “PingFederate” and “Custom,” but using “OneLogin” will work as well.
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>OIDCROPGID</key> <string>9fcc52c7-ee36-4889-8517-lkjslkjoe23</string> <key>OIDCProvider</key> <string>OneLogin</string> <key>OIDCDiscoveryURL</key> <string>https://domain.url.com/.well-known/openid-configuration</string> </dict> </plist>
Once you have the property list file created, save it and run the below command from Terminal to rewrite the property list file into a XML property list file.
plutil -convert xml1 /path/to/property/list/file.plist
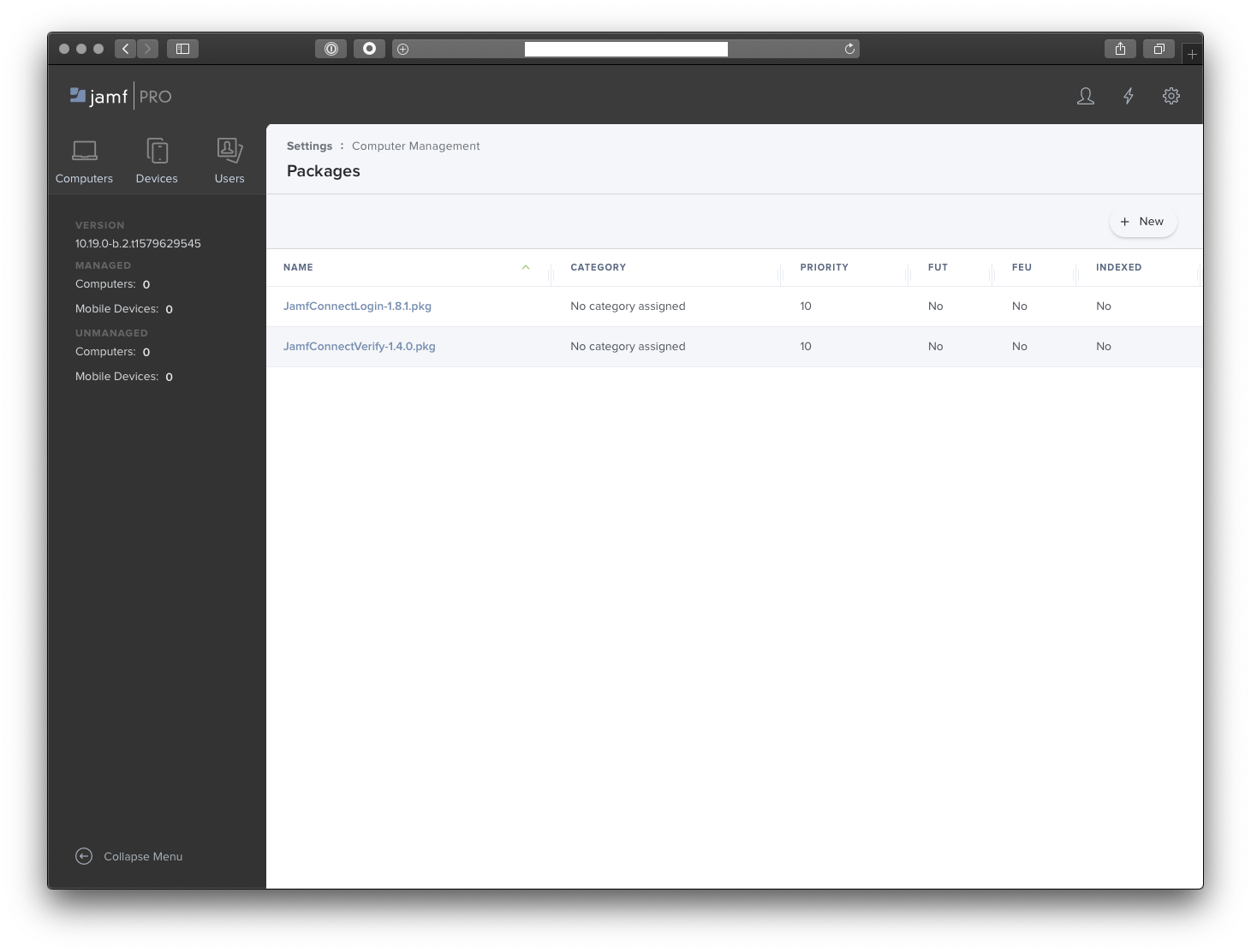
I won’t cover the specifics on deploying this newly created XML property list file as this is already well documented by Jamf here. For reference, Method 1: Use the Application & Custom Settings payload in Jamf Pro was used to create and test the above XML property list file. Another assumption that is made is that you have already uploaded the necessary Jamf Connect License Key and Jamf Connect Verify package into Jamf Pro. For reference, Jamf Connect Verify Version 1.4.0 was used for testing as this was the most recent release at the time of this posting.
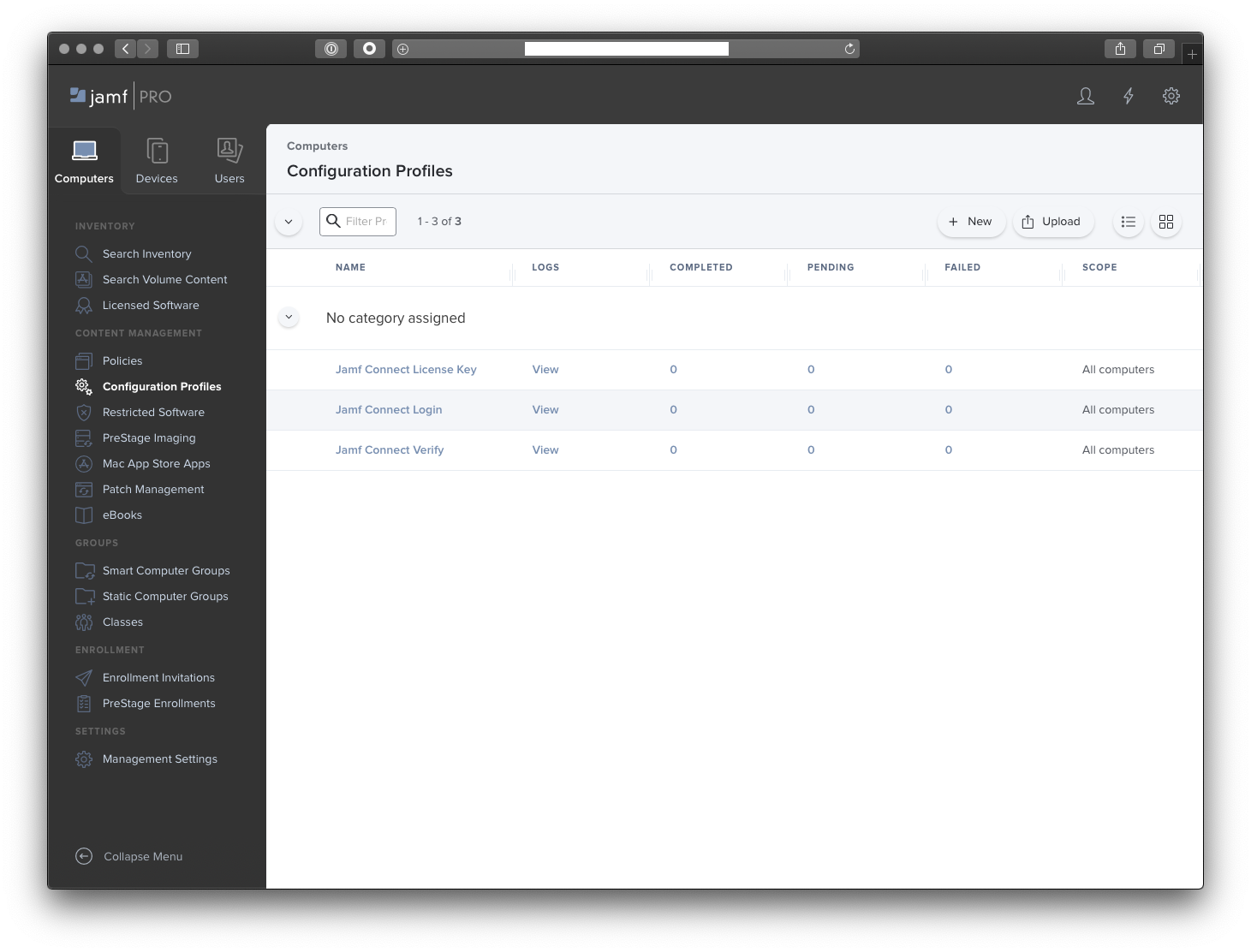
Note: The Jamf Connect License Key is provided by your Jamf account manager. This can be used for all Jamf Connect apps.
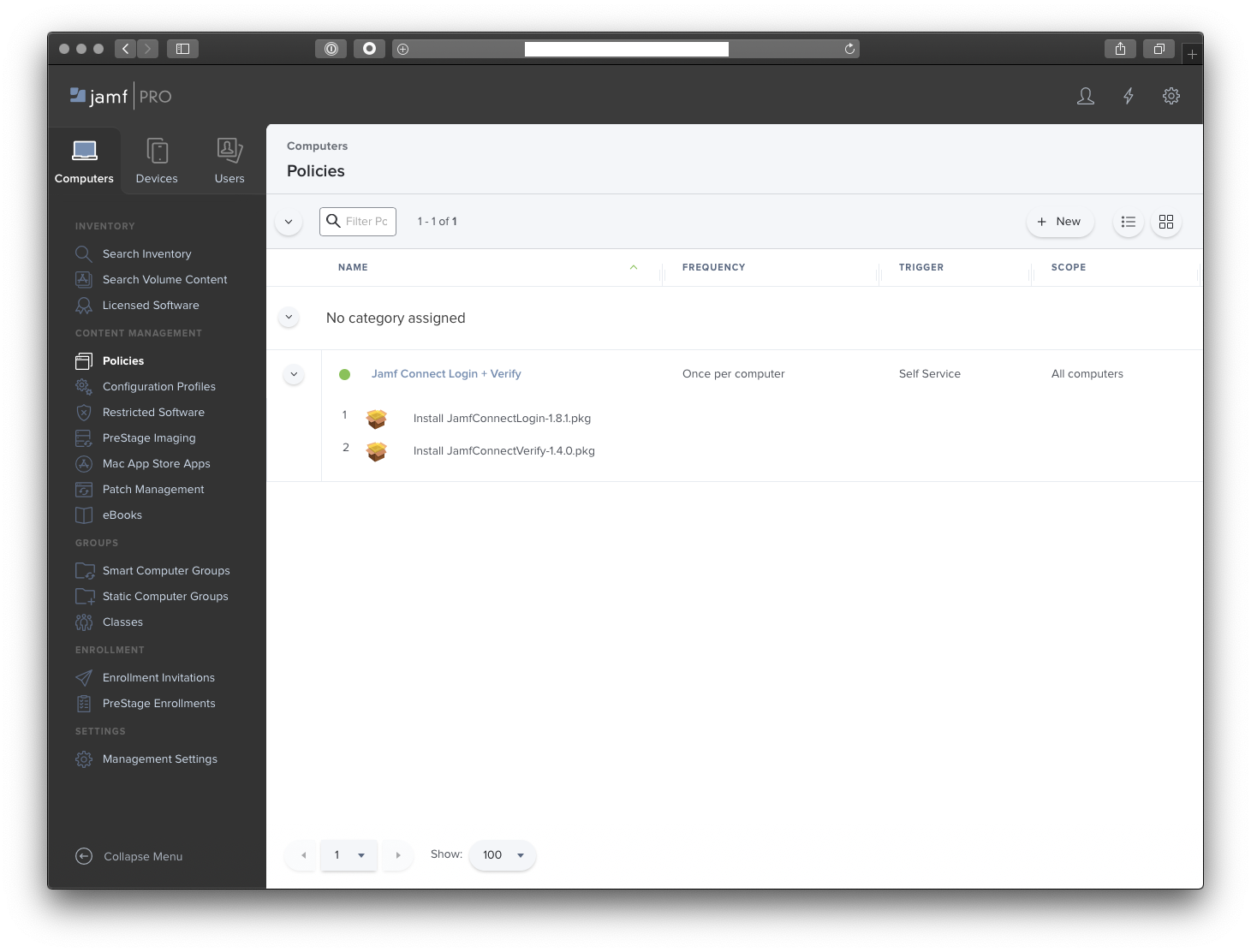
Here is what Jamf Pro should look like after you have created the Jamf Connect License Key and Jamf Connect Verify profiles, uploaded the Jamf Connect Verify package and created a policy to deploy the package.
We are finally ready to test this out! I would strongly recommend using a virtual machine with a tool like VMware Fusion since you will likely have to test this workflow a number of times.
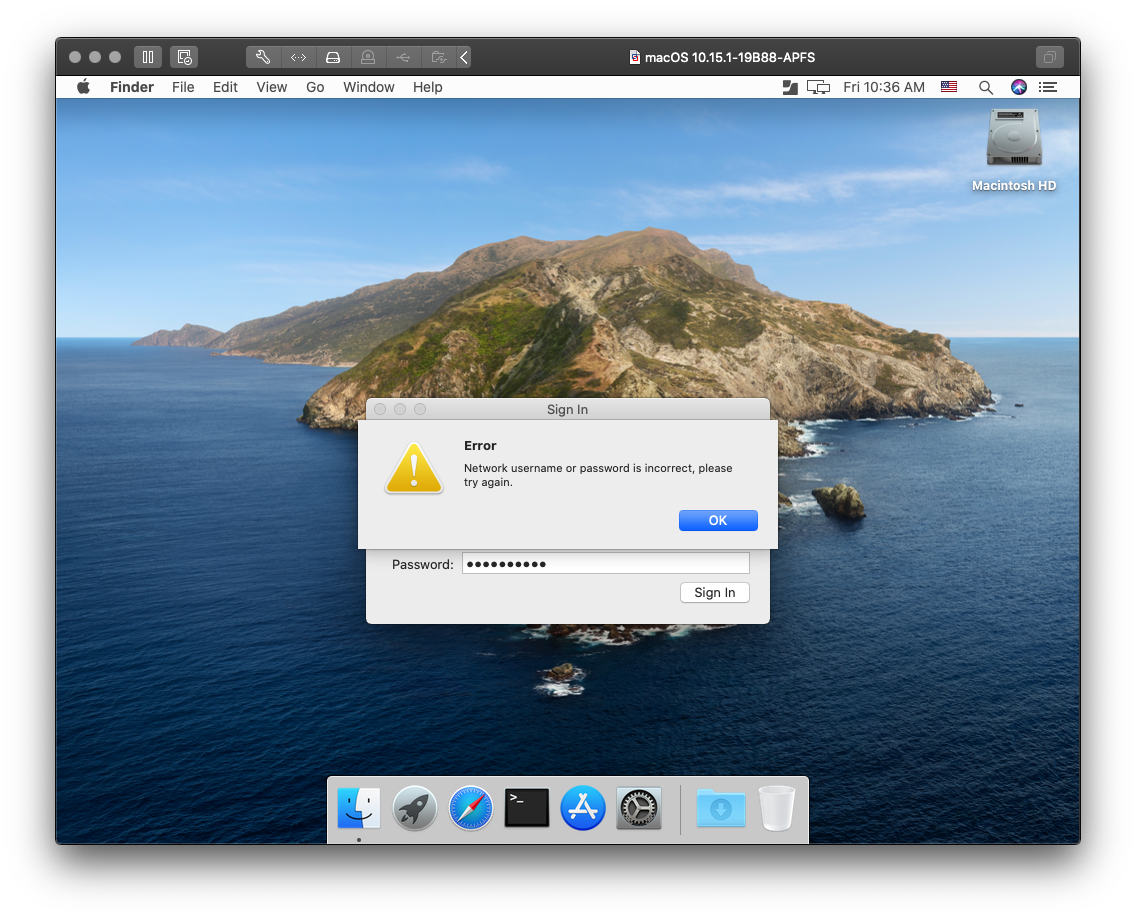
Note: In my testing, I discovered a likely product issue which has since been shared with Jamf Support. If the local password is already the same as the IdP password at the very first login, authentication will fail. I was prompted to sync the passwords by entering in the “network password,” even though they are the same. When the IdP password is entered and matches the local password, I received an error that the password is incorrect. If I quit and relaunch the app, I was able to authenticate successfully.
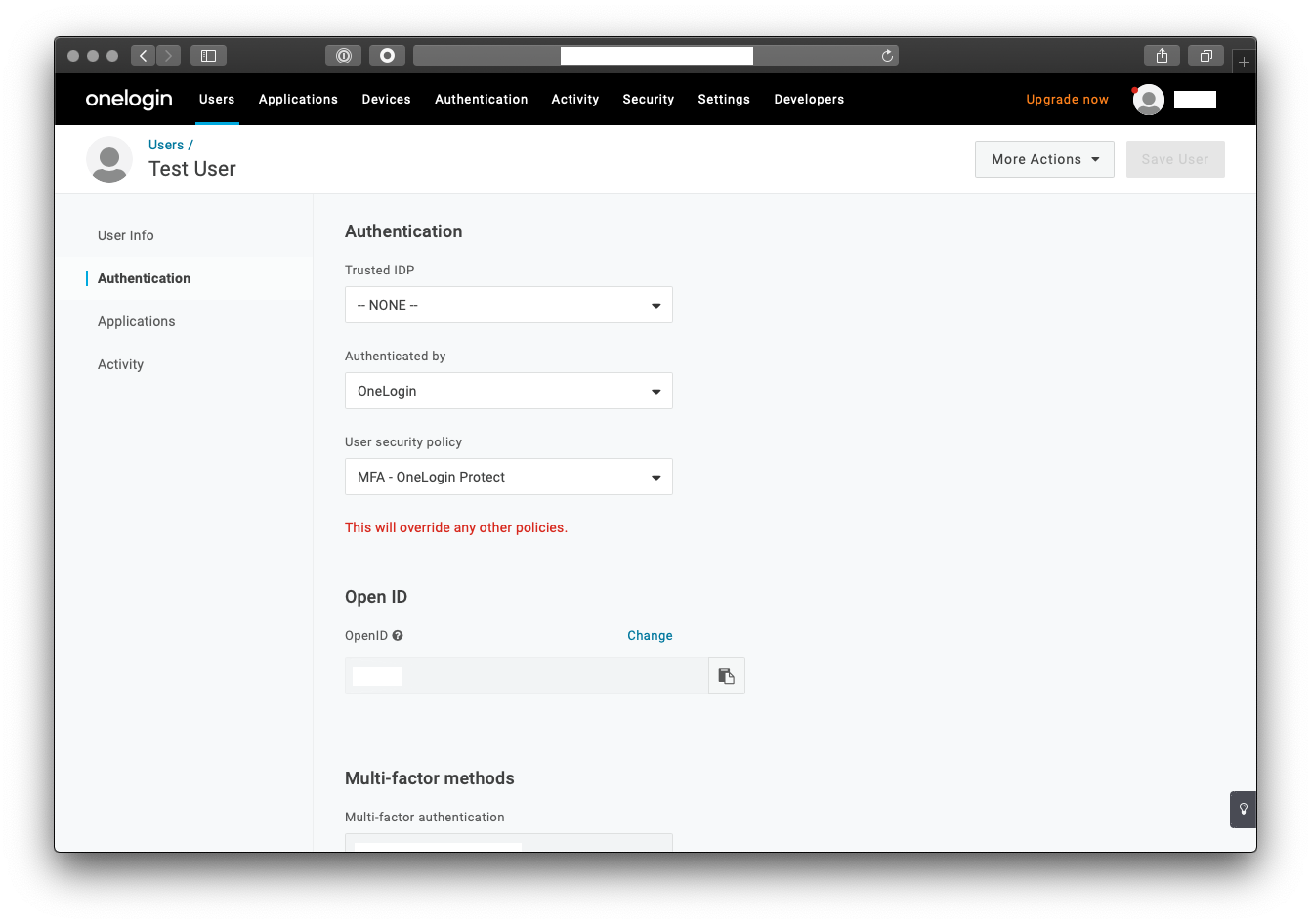
Initially, this worked for me. That is because I did not have multi-factor authentication (MFA) added in my test instance of OneLogin. Since MFA is widely used security add-on for IdP services, I enabled it and noticed that Jamf Connect Verify failed. I was intrigued so I added OneLogin’s native MFA with OneLogin Protect. After running this test again (e.g. quitting Jamf Connect Verify, signing back into Jamf Connect Verify) with the same account after the OneLogin MFA policy was applied to the test user account, this abruptly stopped working. I also tried Google Authenticator to verify whether this was specific to a few MFA types or all MFA options. Sure enough, this also failed.
I ran the verbose command listed below to better understand what was causing this to fail once MFA was applied to the test account. I noticed a MFA specific error at the end, which I shared with Jamf Support.
/Applications/Jamf\ Connect\ Verify.app/Contents/MacOS/Jamf\ Connect\ Verify -v [...] Error: nil Data: Optional(76 bytes) Optional(MFA is required for this user)
After working alongside Jamf Support, I tried making the following ROPGSuccessCodes addition to the previously created property list file.
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>OIDCROPGID</key> <string>9fcc52c7-ee36-4889-8517-lkjslkjoe23</string> <key>OIDCProvider</key> <string>OneLogin</string> <key>OIDCDiscoveryURL</key> <string>https://domain.url.com/.well-known/openid-configuration</string> <key>ROPGSuccessCodes</key> <array> <string>MFA</string> </array> </dict> </plist>
Once the new the property list file was modified, I then saved it and ran the below command from Terminal to rewrite the property list file into a XML property list file. This was then uploaded to Jamf Pro and the configuration profile was reinstalled on my test device. I inspected the configuration profile and tried to sign back into Jamf Connect Verify. Voilà! It worked.
If you are curious like me, you can run the same verbose command from Terminal again with the newly installed Jamf Connect Verify profile. While you will still the error, the “Optional(MFA is required for this user)” portion is nowhere to be seen. This is because the ROPGSuccessCodes value effectively ignores this. This change is what allowed our MFA-enabled account to login. This is how ROPGSuccessCodes was explained to me by Jamf Support.
Error: nil Data: Optional(76 bytes)
Summary
The default Required Key-Value Pairs for Jamf Connect Verify and OneLogin that are listed in Jamf Connect Administrator's Guide for Version 1.15.0 are sufficient if and only if your desired OneLogin user accounts are not configured with MFA. If they are, you will need to add the ROPGSuccessCodes value specified in this post.
I spoke to Jamf Support and requested that the product issue with same local and IdP account passwords be resolved as well as having their product documentation updated to include this ROPGSuccessCodes value as a required field when using MFA. I also requested that Jamf strongly consider officially adding support for Jamf Connect Verify and OneLogin.
My hope is that Jamf will implement these changes as this will help save other IT administrators a great deal of time as well as Jamf Support. Additionally by providing official support for Jamf Connect Verify with OneLogin, I imagine that this will lead to new Jamf Connect clients.